✆ + 1-646-235-9076 ⏱ Mon - Fri: 24h/day
Why CEOs Need to Understand Zero Trust – Even If They’re Not Engineers


Cybersecurity means so much in 2025. It is a technical concern, a business risk, a financial liability, and a legal obligation more often than ever before. Among all modern security paradigms, Zero Trust has become the most important framework for protecting company data, employee access, customer information, and digital assets.
Even CEOs who never write a line of code need to understand it, because Zero Trust affects compliance, insurance eligibility, company valuation, and operational stability.
This article explains Zero Trust in simple, business-friendly terms and shows why an understanding of this model is essential for responsible leadership.
What Is Zero Trust and Why Is It Important
Zero Trust is a cybersecurity framework built on a simple idea:
Never trust anything automatically. Verify. Always.
In old-school security, once someone passed the firewall, they could roam freely inside the network.
Zero Trust flips this logic and assumes:
- No device is trusted by default
- No user is trusted by default
- No application is trusted by default
- Access is granted only when verified, and only to what is strictly necessary
Why This Matters
According to the Verizon Data Breach Investigations Report 2023, 74% of all breaches involve the human element (error, privilege misuse, stolen credentials, or social engineering).
Another study by Mimecast states that 95% of cybersecurity breaches involve human error.
Today’s threats don’t come only from “the outside.” Modern risks include:
- stolen credentials
- misconfigured VPNs and cloud services
- insider attacks
- exploited access tokens
- compromised laptops or mobile phones
- infected IoT sensors or employee devices
That means that most likely your company’s security one day will be compromised on a human level.
Zero Trust protects companies against these scenarios by enforcing continuous authentication, least privilege, segmenting data, and reducing the “blast radius” of any breach.
In business terms:
Zero Trust is insurance, resilience, and reputation protection.
To understand this model more easily, let’s think about a regular company’s security system as a bubble. Once you’re inside, you can do almost anything you like.
If we talk about the Zero Trust model, you should think about it as a honeycomb. Your company’s security system makes your departments and resources look like isolated hexagons. Even if one component has been compromised, the keys will be changed soon, and the scope of compromised resources is very limited.


Source: Image generated by AI
When Do You Need a Zero-Trust Model? Who Needs It Most?
Zero Trust is becoming a default expectation for any modern organization, but it is especially important for companies that:
Handle sensitive data
- Healthcare providers
- Insurance companies
- FinTech platforms
- Legal and government agencies
- E-commerce companies storing payment information
Have remote or hybrid employees
Every remote login is a new doorway. Zero Trust makes each doorway secure.
Operate globally
Compliance requirements differ across regions, and Zero Trust satisfies most of them.
Rely on cloud or distributed systems
Cloud environments expand the attack surface. Zero Trust shrinks it back down.
Use IoT or smart devices
Connected devices can be compromised, so every device must authenticate continuously.
Serve enterprise clients
Many large corporations will not sign a contract unless your company follows Zero Trust principles.
When Is Zero Trust Legally Required? Why Should CEOs Care?
The Zero Trust model affects legal compliance, certifications, and contract eligibility.
A CEO must understand Zero Trust because:
• It is becoming a compliance baseline
Industries like healthcare and finance increasingly expect Zero Trust practices for regulatory compliance.
For example:
- HIPAA (healthcare) strongly aligns with Zero Trust principles
- GDPR (EU) requires “data minimization” and strict access controls
- PCI-DSS (payments) demands least-privilege, segmentation, and ongoing verification
• Insurance companies require it
Cyber-insurance providers often refuse claims if the organization did not implement adequate access controls, MFA, or identity verification of all core Zero Trust components.
• It reduces financial risk
The average global data breach now costs $4.45 million (IBM Security 2024 report).
Zero Trust can reduce breach impact by up to 40%, according to IBM.
• It protects valuation during investments or acquisitions
Investors now ask:
“Is your infrastructure secure enough to scale?”
A breach before or during acquisition can drop valuation by millions.
• It protects operational continuity
If your product relies on cloud APIs, IoT devices, or remote staff, a single compromised account can shut down your business. So, CEOs must care because Zero Trust impacts revenue, lawsuits, insurance, client trust, and corporate survival.
Example of a Flexible Zero-Trust-Friendly AWS Architecture for Healthcare
Unlike traditional infrastructures, where services trust each other once inside the network, a Zero Trust environment requires every user, device, and service to authenticate and authorize on every request using temporary credentials, short-lived certificates, and tightly scoped IAM policies.
This AWS architecture demonstrates how a healthcare application can securely operate under Zero Trust requirements.
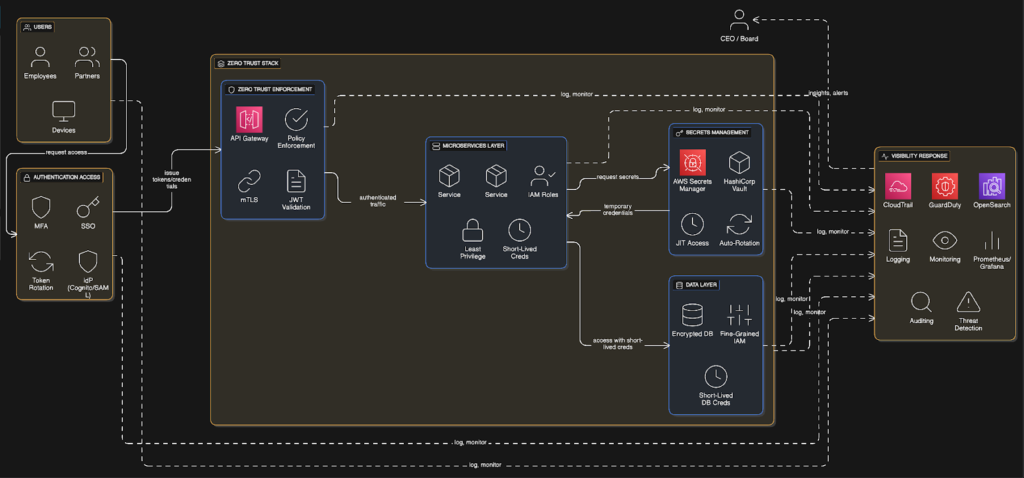

So, Zero Trust:
- No internal service trusts another without explicit authentication
- All data is encrypted at rest and in transit
- IAM enforces least privilege
- Every request is validated
- Audit logging tracks every action
- Network segmentation limits lateral movement
Why healthcare needs this:
Because a leaked medical record contains names, addresses, insurance details, SSNs, and diagnoses, exactly the type of information criminals value most.
How Fordewind.io Helps Companies Implement Zero Trust Successfully
Fordewind.io has practical experience implementing Zero Trust in organizations of all sizes, from startups to large enterprises.
We’ve delivered secure infrastructures for:
- Healthcare platforms (HIPAA-aligned)
- FinTech solutions
- Global e-commerce systems
- EV charging networks
- Smart home ecosystems
- Automotive IoT sensors (Mitsubishi, charging stations, telematics)
- Access control and smart lock systems
What We Provide
- Zero Trust design and implementation
- Identity and access management (MFA, IAM, SSO, least privilege)
- Secure cloud and hybrid architectures
- Threat modeling and risk assessment
- Compliance-driven infrastructure (HIPAA, GDPR, PCI)
- Audit logging, monitoring, and encryption policies
- IoT device identity, certificates, and secure communication
We design systems that remain secure, scalable, and flexible without slowing down product delivery.
Conclusion
In conclusion, CEOs don’t need to understand the technical implementation, but they absolutely must understand the business value, legal implications, and risk reduction that Zero Trust provides.
Zero Trust is how companies protect revenue, reputation, and operational continuity.
With its deep experience across healthcare, finance, IoT, and high-security domains, Fordewind.io helps organizations adopt Zero Trust in a way that is practical, business-driven, and future-proof without unnecessary complexity or cost.